The Reliability Engineer’s Guide to Understanding IIoT Device, LAN, and WAN Security
Table of Contents

As wireless sensor technology begins to take the leading edge within the industrial internet of things community, a new era of data security has emerged that requires diligent thought and consideration on the part of end users, system integrators, and key stakeholders.
Critical machine health and process data being transmitted wirelessly and hosted internally as well as externally creates an entirely new series of security concerns that must clearly be understood to maximize the value of the technology.
This presentation will focus on the key security tools available to end users to ensure the security of their data when deploying wireless sensor networks and hosting data internally as well as externally to their organizations.
What is Bluetooth?
Bluetooth allows computers talk to each other seamlessly (Svetlik, 2018), which according to (Wikipedia, 2020), is a wireless technology standard used for exchanging data between fixed and mobile devices over short distances, using the UHF radio waves in the industrial, scientific and medical radio bands, from 2.402 GHz to 2.480 GHz, and in building personal area networks (PANs). It is commonly found in smart phones, smart watches, wireless headphones, wireless speakers, etc. It is a primary mode of communication in smart homes and for internet of things (IIoTs) technology.
Bluetooth 5.0 is the latest version of the Bluetooth wireless communication standard (Hoffman, 2018) and thus serves as a common communication feature for the latest smart phones, smart gadgets and IIoT devices. Bluetooth technology is in itself backward compatible, where older versions and devices can still function/communicate with a device having the latest version enabled. Thus the overall advantage to be gleaned from using the latest version (Bluetooth 5.0) cannot be enjoyed without compatible peripherals.
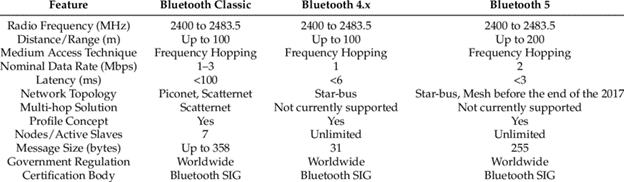
Fig 1 depicts a comparison amongst the various versions of Bluetooth, where there are clear improvements in latency of less than 3ms compared to the 6ms in Bluetooth 4.X and 100ms in the Bluetooth classic, an increase in maximum distance/range of up to 200metres, compared to 100metres in both Bluetooth 4.X and Bluetooth classic respectively. A majority of the improvements to Bluetooth technology has been in the Bluetooth low energy specification. Where, Bluetooth 5.0 enables all audio devices connected to it to communicate over Bluetooth low energy rather than over the power hungry Bluetooth classic standard, thus reducing power usage and the resultant longer battery life. Other related benefits to Bluetooth 5.0 includes, the dual audio feature, which allows users to play audio on two connected devices at the same time, data transfer speeds of up to 2Mbps, eight times the broadcast message capacity of older versions of Bluetooth etc.
Wireless sensors networks are interconnected sensor nodes which communicate wirelessly to collect data about its environment (Harsh Kupwade & Thomas, 2017). The Core of an IIoT implementation are wireless nodes. Where these nodes are generally low power, and distributed in an ad hoc decentralized fashion. Security is a major challenge for IIoT networks owing to the number of “things” and the openness of the system. Security concerns are related but not limited to issues such as privacy, authentication, and access control.
ERBESSD INSTRUMENTS PHANTOM WIRELESS MACHINE SURVIELLANCE
According to (ERBESSD INSTRUMENTS, 2020), the Phantom is an advanced, highly flexible solution for increasingly demanding Ultra Low Power, Secure, Ultra Long Range, and higher throughput applications in the IIoT world

Phantom has an embedded cryptographic accelerator for providing high grade security specifications. Specific features of the Phantom and its sister modules relates to data rates (2Mbps, 1Mbps, 500Kbps, 125Kbps), memory (1MB of flash memory, 256KB RAM), 48GPIO pins, 1.7V to 3.6V DC supply, 255 broadcasting message length , forward error correction (FEC) coding using Bluetooth SIG CORE_v5.0 LE CODED PHY, range of 650metres using the PCB trace antenna, a high voltage power supply to accept up to 5.5V DC for direct connection to a lithium battery or a 5V power source, an Embedded CryptoCell 310 co-processor to provide a more secure connection and to prevent hackers.
The Phantom’s most importantly offers a cost effective solution for IIoT product implementations at different ranges with its low prices. No change is required on the main board hardware for any implementation, thus ensuring that it is modular in design and implementation.
SECURITY ELEMENTS AND CONSIDERATIONS OF BLUETOOTH 5
According to the report in (INSTRUMENTS, 2020), the vulnerabilities facing BLE 5.0 are deemed very high and more so due to the various benefits and capabilities of Bluetooth 5.0 technology, which has made it a primary communication medium of choice for connected devices, as opposed to Wi-Fi. The increased bandwidth and connection distance has been a source of vulnerability, because attackers can access Bluetooth connections from a long distance away, and with fast data transfer speed, can wreak havoc without notice. According to NIST report, (NIST, 2012) common areas of vulnerabilities in traditional Bluetooth 5.0 are as follows:
- Lack of end to end security
- No user authentication
- Insecure storage of link keys
- Discoverable devices
The lack of end to end security is a major vulnerability of the traditional BLE system. The current system implements individual link encryption, with message decryption at intermediate points on the communication link that could lead to an intermediary attack (MITM), also the absence of application and user level authentication as a default in the Bluetooth specification is also an area of vulnerability, as the currently offered device level authentication isn’t sufficient nor impervious to malicious attacks, possibility of data corruption during improper synchronization, potential for loss of data stored on an IIoT device if stolen are all very critical.
Man in the middle (MITM) attacks can be mitigated by the deployment of user input passkeys, although passkey linking isn’t applicable for applications without a keypad or a display, passkeys are also not well suited for passive eavesdropping attacks. Passive eavesdropping attacks are attacks which are a little different from man in middle attacks, in that the eavesdropper doesn’t intend to change or impersonate data; rather he/she sits idly, while gathering information. (INSTRUMENTS, 2020) Surmises that at least 80% of all Bluetooth enabled smart devices are vulnerable to man in the middle attacks (MITM).
Data transmission over the Bluetooth 5.0 uses AES-CCM encryption, where this encryption takes place in the Bluetooth controller. Bluetooth low energy encryption security modes are of two types; namely the LE security mode 1 and the LE security mode 2 as shown in fig 3.
LE security mode 1 has four security levels, namely the no security (no authentication, no encryption mode), the unauthenticated pairing with encryption, the authenticated pairing with encryption and lastly the Authenticated LE Secure Connections pairing with encryption using a 128-bit strength encryption key. Where, each security level satisfies the requirements for the level below it.
LE security modes /levels and their associated characteristics are depicted in fig 4.
Figure 3: LE Security mode (INSTRUMENTS, 2020)
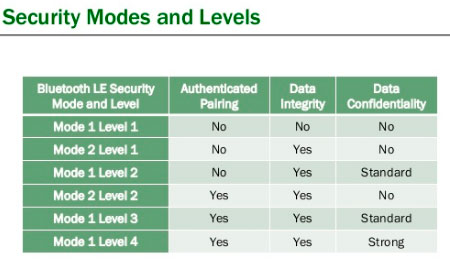
Figure 4: Security Modes and Levels
In LE security mode 2, it consists of two security levels, namely the unauthenticated pairing with data signing and the authenticated pairing with data signing. It is mainly used for transferring data between two devices on an unencrypted connection.
Elliptic Curve Diffie-Helman cryptography is used for key exchange in Bluetooth LE Secure Connections, according to the Bluetooth Specification Version 5.0. This helps protect against passive eavesdropping but, may be susceptible to Man in the Middle (MITM) attacks. However to prevent that, random passkey generation is recommended each time pairing is initiated, where the ‘master’ and ‘slave’ device will each generate a 128-bit random number, which will serve as a temporary key (TK).
PHANTOM SECURITY ELEMENTS AND CONSIDERATIONS
Encryption, decryption and authentication are handled in the Phantom Eco-System by the Cryptocel-310 in order to deliver high performance in Bluetooth mesh networks. The Bluetooth mesh network already has some security features such as encryption and authentication of all mesh messages, independent addressing of network security, device security and application security, key refresh procedures, message obfuscation, secure creation of nodes in a mesh network, secure removal of node in the mesh network to prevent trash can attacks. The security protocols of mesh networks or individual applications with Bluetooth 5.0 cannot be reduced or switched off, thus it is always ever present.
To achieve a separation of concerns, three different security keys provide security to different aspects of the mesh namely, the network key (NETKEY), which allows a node to encrypt and authenticate up to the network layer, the application key (APPKEY), which allows a node to decrypt application data, and the device key (DEVKEY) , which is unique to each node, and allows for secure communication with the provisioner in a provisioning process
Due to the processing power requirement for decryption and authentication, the Phantom and its related sister modules use the ARM cryptocell-310 cryptographic co-processor to achieve mesh network performance. Features such as secure boot, key management infrastructure, device life-cycle-state management, cryptography and security middleware service, cryptographic hardware engines, etc are critical for the high performance delivered by the Phantom on security and possible network vulnerabilities.
The emergence of LE technology in Bluetooth 4.X till the current specification of 5.0, has ensured that peripheral devices no longer need the same memory or processing power requirement than the central unit (sender). Single mode peripheral devices have gained the most advantage (Ravikiran, 2020), thus peripherals can be designed with low memory, longer battery life and even as low power consumption smart wearable devices. These peripherals are classified as Bluetooth smart ready devices as shown in fig 4
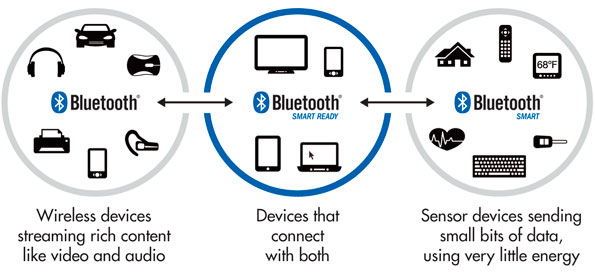
Figure 4: Bluetooth Smart Ready Network
The four levels of security as well as the two security modes imply there are always considerations for the mode to be applied to a peripheral device. The secure connection mode, which involves security mode 1, level 4 will ensure there is an authentication and encryption for all communication between the sender and the receiver, however this will mean more computational power needs and a resultant power drain for battery powered devices. Thus, there must be a compromise with whether encryption without signing will be sufficient. Phantom balances both the needs of security and battery life by combining the cryptocell 310 co-processor for cryptographic processes and the high-performance lithium ion battery that is field replaceable.
The pairing process between a peripheral device and a sender with a Bluetooth connection involves three phases namely; phase one, where each device makes the other aware of their capabilities captured in their individual attribution protocol (ATT) values, secondly the phase two, where a long term key (secure connection) or short term key (insecure connection) is generated after the devices have agreed on a mixed random number called the temporary key (TK), thirdly the phase three, where the connection signature resolving key (CSRK) used for data signing and the identity resolving key (IRK) used for private MAC address generation and lookup are all generated respectively (Mark, 2018).
Once the keys have been generated , there are four pairing modes, namely, numeric comparison ( which involves matching a six digit number generated by both devices), just works ( a very popular method that’s very popular method which is to put the six-digit number to all zeros for both devices ), passkey entry ( a six digit number from one device which must be entered into the receiver device for communication ) and the out of band (OOB), which is using a communication channel outside the main stream Bluetooth channels. The entire pairing process is as shown in fig 5
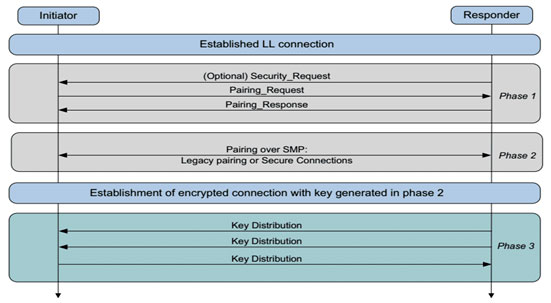
Figure 5: Bluetooth Pairing (Kai, 2016)
The Phantom will always have a peripheral similar to it, with limited display capability in the case of the gateway and no keypad, thus the most appropriate security protocol is to implement a key distribution pairing protocol
LAN/WAN NETWORK SECURITY
LAN/WAN NETWORK SECURITY
A Firewall is a network security system that monitors incoming and outgoing network traffic based on predefined security rules (concept draw, 2020). It establishes a barrier between an internal network which is trusted and an untrusted network such as the internet or another wireless communication technology such as Bluetooth. Firewalls exist as either network firewalls or host based firewalls. A typical depiction of a firewall between a LAN and a WAN is as shown in fig 6
Figure 6: LAN and WAN Security Firewall (concept draw, 2020)
According to (Walter, 2005), obvious threats to information security are those concerning data while being transmitted over a network. Examples of some of these security threats for WANs and LANs are but not limited to; wire tapping – physical attempt to breach a communication medium for the sole purpose of data interception and malware injection, masquerading – an entity that pretends to be another entity, modification of messages- altering of transmitted data without being detected, replay of messages – an attempt to repeat messages in order to result into something undesirable, denial of service – a node fails to perform its proper function or acts in a way that prevents other nodes from performing their proper functions, trapdoors and Trojan horses – When an entity is modified to allow an attacker to produce an unauthorized effect on command or at a predetermined event.
The use of additional security protocols asides using firewalls are also encouraged, where examples of these are; the use of WPA or WPA2 for password encryption on all traffic incoming or outgoing to the internet, filtering of traffic using detailed knowledge of trusted sources, this is usually achieved using specialized authentication policies, using tunnel technologies such as VPN, packet control through different areas of the OSI model, MAC address trust protocol, and internal security features such as antivirus and antimalware programs.
As much as the use and deployment of virtual personal networks (VPN) helps to provide some form of security over a WAN network, it is advisable to adopt software defined –WAN, which is a centralized network control system that enables agile, real-time application traffic management without overhauling an existing WAN. SD-WANs also enable access to cloud applications without causing the data bottlenecks a traditional WAN would.
ENTERPRISE NETWORK DEVICE SECURITY
Security for cloud based services can be classified into three areas of vulnerabilities. The physical security protocol, establishes protocols for the protection of physical assets at a geographical location, infrastructure security, establishes protocols for the ensuring that security patches are updated as soon as possible, ports are scanned for abnormal behavior and data and access security deals with data encryption and user privileges control.
Cloud services are remotely hosted , run and managed by leading tech companies, and this sometimes gives the false belief that it is impervious to security challenges. (Fred, 2018) highlights some security challenges that cloud services face such as; data breaches, human errors, data loss with no backup, insider threats, DDoS attacks, insecure API’s, exploits, account hijacking, advanced persistent threats and meltdowns.
While there are numerous benefits to using a cloud based service such as Amazon cloud services (AWS) and Microsoft azure, they take security seriously and try to implement some protocols that protect data transmitted and stored in their infrastructure.
AWS adopts isolation as its main security mantra (Sarapremashish, 2020), this ensures that customers cannot access any other resource within their network unless they explicitly enable such access. Isolation is achieved by accounts, which are completed islanded from each other , except in cases where customers have inter-service access. However despite this isolative security tact, AWS still implements security groups such as firewalls, granular identity and access management (IAM). AWS provides lots of security tools, such as AWS Config, CloudWatch, CloudTrail, GuardDuty, Macie, and Security Hub. Dependability is another AWS asset as it regularly exhibits rock-solid performance and consistency
Microsoft Azure, on the other hand is its adoption of an azure active directory which is the singular platform for authorization and permissions management, but it still has some vulnerability as ports and destinations are left open and exposed to the internet, during default initiation.
According to (Michael, 2020), Microsoft has more than 3,500 cybersecurity experts working to keep Azure secure and an extensive threat intelligence operation that includes analysis of 18 billion Bing web pages, 400 billion emails, a billion Windows device updates, and 450 billion monthly authentications. The azure system also improves its security by ensuring tight controls on setting up user accounts, where they restrict the opening of multiple accounts with the same domain email.
CONCLUSION
The Phantom Eco-System is an advanced solution for high throughput applications in IIoT’s today. It is equipped with the latest technologies which ensure robust network protection, prevention of data obfuscation, and support suitability for implementing the latest Bluetooth 5.0 security protocols based on the application of use. LAN’s and WAN’s are a primary method for data communication over the internet in an IoT implementation, thus security features such as firewalls and software defined WAN’s are cost effective and reliable solution to managing security issues that could compromise an IoT implementation. Microsoft Azure, although with its positives with respect to fast configuration time, has security vulnerabilities, which for all intensive purposes are well handled in AWS.
AWS has been a long time player in the cloud space and thus have more optimized processes as well as optimized security protocols that would ensure end to end protection of data and the entire communication network.
Dr. Michael Howard, is an American entrepreneur and Air Force veteran with a remarkable career in the predictive maintenance industry spanning over 30 years, and a variety of industrial sectors, including industrial manufacturing, reliability engineering, and instrumentation development and design organizations. Dr. Howard is a graduate of Excelsior University, Capella University, and New Charter University with degrees in Electro-Mechanical Engineering, Leadership and Organizational Management, and Engineering Management.
As the CEO of Erbessd Instruments, he leads strategy, sales, marketing, and operations in English-speaking markets. He is a certified reliability engineer, certified maintenance and reliability professional, and category III vibration analyst. Michael is a passionate advocate for wireless instrumentation, video deflection, and the Industrial Internet of Things (IIoT).
ERBESSD INSTRUMENTS® is a leading manufacturer of Vibration Analysis Equipment, Dynamic Balancing Machines, and Condition Monitoring with facilities in Mexico, the USA, the United Kingdom, and India.












