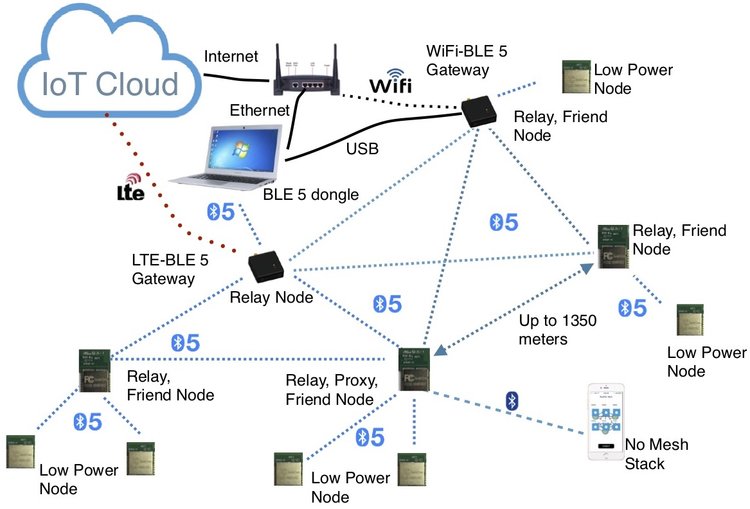
Wireless Sensor System Security… Essential…
Table of Contents
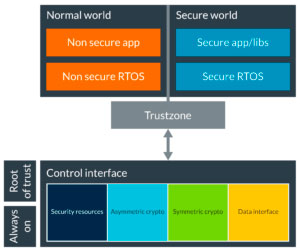
Security is mandatory in Bluetooth mesh networks. Phantom features Unparalleled Security Features.
By offloading decryption, encryption, and authentication works to our CryptoCell-310, Phantom can deliver high performance in Bluetooth mesh networks.
Mesh network, individual applications, and Bluetooth 5 devices are all secure. This cannot be switched off or reduced in anyway.
- All mesh messages are encrypted and authenticated.
- Network security, application security, and device security are addressed independently.
- Security keys can be changed during the life of the mesh network via a Key Refresh procedure.
- Message obfuscation makes it difficult to track messages sent within the network providing a privacy mechanism to make it difficult to track nodes.
- Mesh security protects the network against replay attacks.
- The process by which devices are added to the mesh network to become nodes, is itself a secure process.
- Nodes can be removed from network securely, in a way which prevents trash can attacks.
Three security keys provide security to different aspects of the mesh and achieve a critical capability in mesh security, that of “separation of concerns”.
- NetKey (network key) possessed by all nodes. It allows a node to decrypt and authenticate up to the Network Layer. A Relay node uses NetKey to decrypt and authenticate messages before relaying.
- AppKey (application key). Application data for specific application can only be decrypted by nodes possess the right AppKey.
- DevKey (device key) is unique to each node. It is used for secure communication with the Provisioner during provisioning process.
In a mesh network with many nodes, a lot of processing power is required for decryption and authentication at least for the Relay nodes and possibly for other nodes. Phantom is embedded with an ARM CryptoCell-310 cryptographic co-processor. To achieve acceptable mesh network performance, Phantom should be used in mesh networks with many nodes.
CryptoCell-310 provides the following key features:
- Cryptographic hardware engines, providing CPU host offloading, operation, acceleration and power consumption reduction.
- Cryptography and security middleware services
- Platform Security building blocks libraries
- Device Life-Cycle-State management
- Key Management infrastructure
- Secure Boot.
By offloading decryption, encryption, and authentication works to CryptoCell-310, Phantom can deliver the highest performing security of all Bluetooth mesh wireless sensor networks.
Dr. Michael Howard, is an American entrepreneur and Air Force veteran with a remarkable career in the predictive maintenance industry spanning over 30 years, and a variety of industrial sectors, including industrial manufacturing, reliability engineering, and instrumentation development and design organizations. Dr. Howard is a graduate of Excelsior University, Capella University, and New Charter University with degrees in Electro-Mechanical Engineering, Leadership and Organizational Management, and Engineering Management.
As the CEO of Erbessd Instruments, he leads strategy, sales, marketing, and operations in English-speaking markets. He is a certified reliability engineer, certified maintenance and reliability professional, and category III vibration analyst. Michael is a passionate advocate for wireless instrumentation, video deflection, and the Industrial Internet of Things (IIoT).
ERBESSD INSTRUMENTS® is a leading manufacturer of Vibration Analysis Equipment, Dynamic Balancing Machines, and Condition Monitoring with facilities in Mexico, the USA, the United Kingdom, and India.








